Virus checks
Virus checks are performed automatically when files are uploaded
A virus check is run on a file every time it is uploaded. This reduces the risk of a virus infection spreading.
File encryption
All files are stored in encrypted form
As files are stored in encrypted form, they are safely protected from outside attacks and network-borne risks.
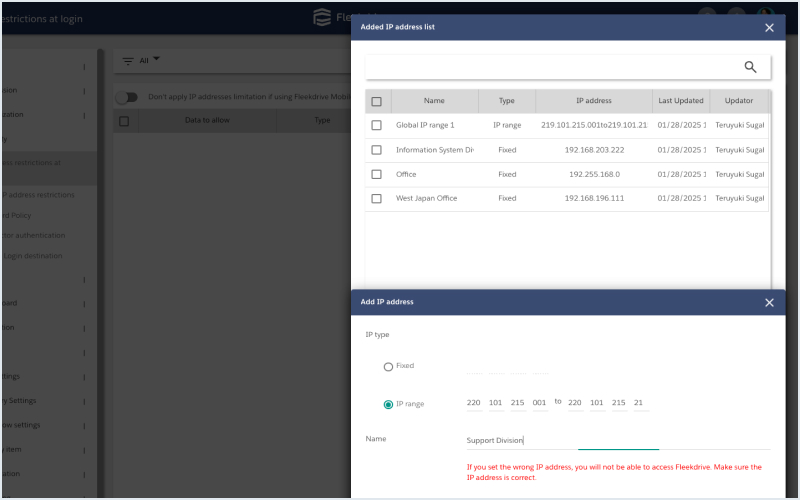
IP address restriction
Restrict source IP addresses allowed access for safety and security
Access from certain IP addresses can be restricted. For example, you can allow access from a pre-designated IP address and restrict access from other such as Internet cafes and overseas. Source IP addresses can be restricted on a per-folder basis.
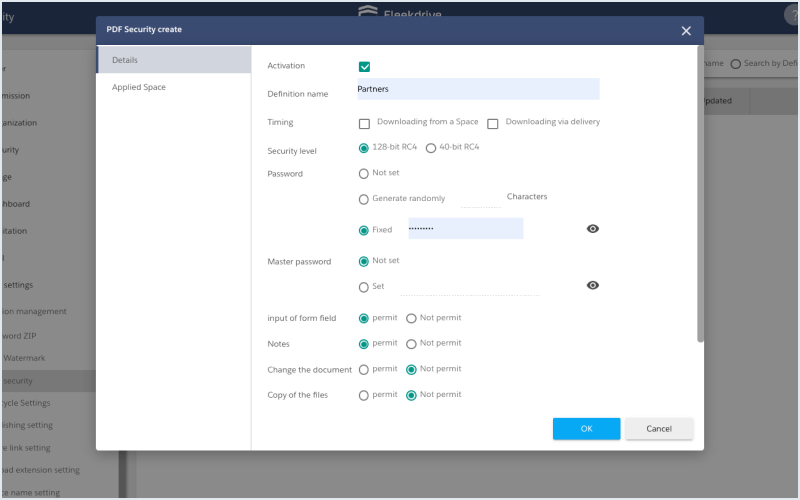
PDF security
Prevent the leak of information by restricting the copying and printing of PDFs
Security settings such as encryption and not allowing printing can be set for when a PDF file is downloaded. Security features on PDF files such as not allowing printing or copy & pasting prevent information leaks and other issues.
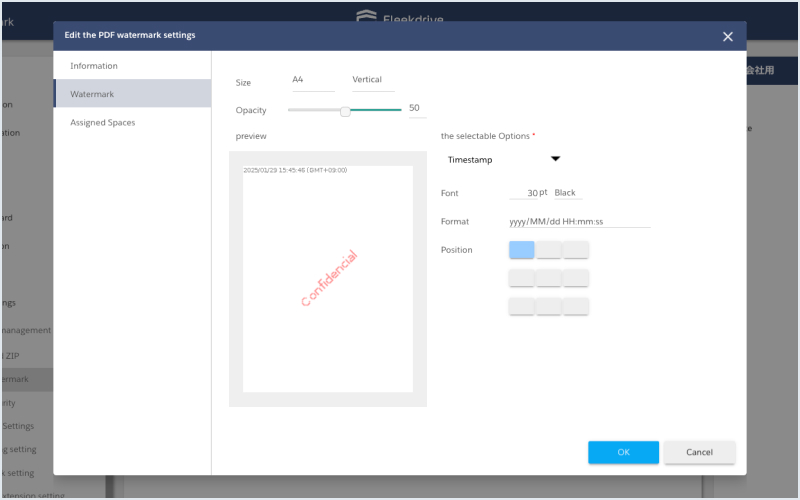
PDF watermarking
Manage PDFs taken beyond your own infrastructure by displaying user information or other data
When a PDF file is downloaded, it can be watermarked with text including the date and time of download, user ID and other information. This lets users put in place restrictions on how important files are taken beyond their own infrastructure, and makes it possible to track a file on the outside.
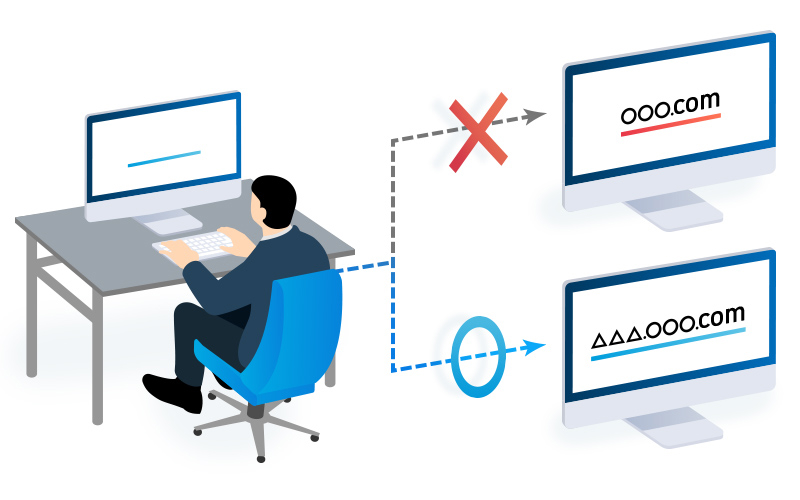
Sub-domain operation
Restrict the cloud usage of permanent in-house partners
Users can set up their own subdomain. This allows you to restrict access to Fleekdrive by resident partners outside of your company by only allowing access from subdomains.
*It requires IP address control and whitelist registration on the part of the customer.
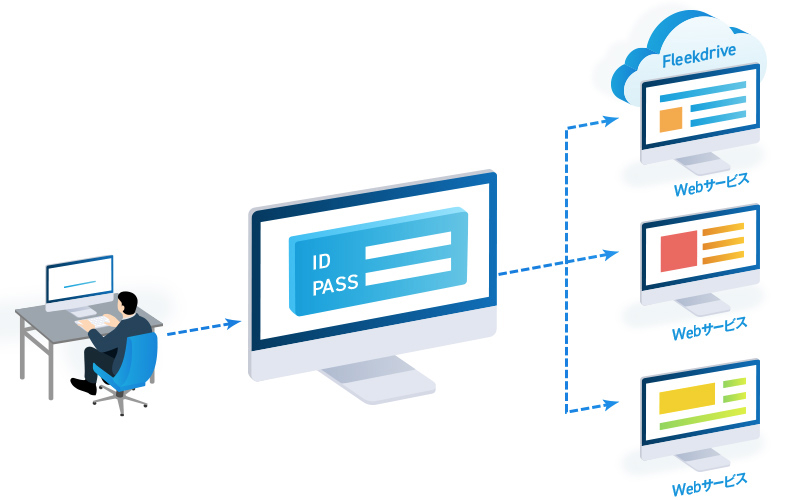
Single sign-on
Enhanced security with centrally managed IDs and passwords
Users can login to Fleekdrive based on authentication information from an integrated service. This allows Fleekdrive to be used without requiring additional authentication, removing the need to remember several IDs and passwords, and enabling the use of multiple services without hassle. This feature is also expected to strengthen security by reducing the recycling of passwords across multiple services.
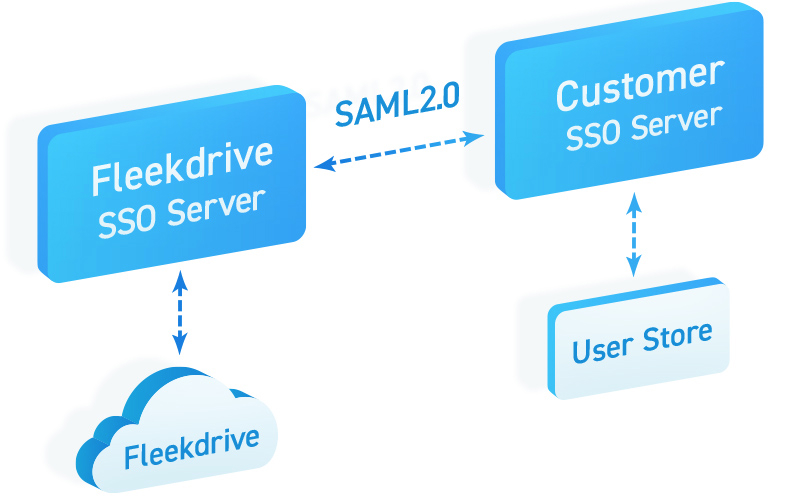
Single sign-on (in-development feature)
Compliance with SAML 2.0 enables integration with various ID providers
Fleekdrive employs single sign-on (SSO authentication), allowing users to seamlessly log in to multiple apps with a single set of credentials.
SSO is supported through SAML 2.0, which has a track record of integration with various third party ID providers.
Track record: ADFS, OneLogin, HENNGE One, SeciossLink, Trust Login, CloudGate UNO, etc.
Optional auditing
Receive automatic notification of suspicious actions 24/7
When the items to be monitored are set, the system detects suspicious user actions and automatically sends out a notification. For example, when abnormal behavior is detected, such as a user from a partner company accessing files outside business hours, or large file downloads late at night, an administrator can be notified in real-time.
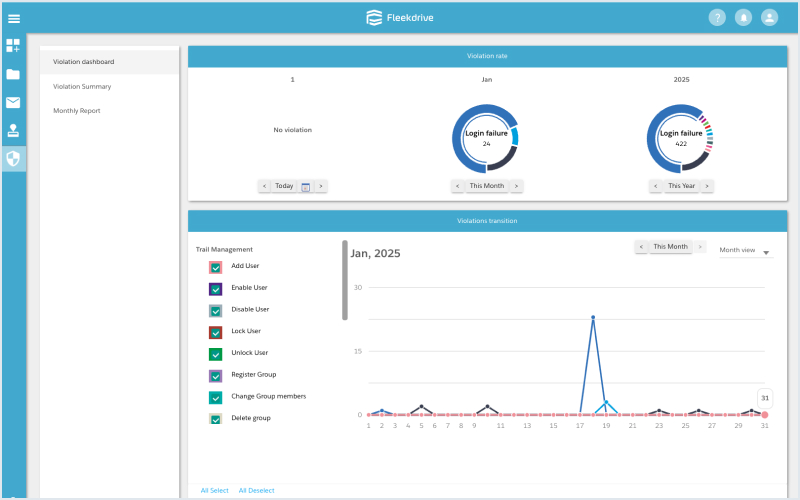
Traceability feature
Visualize all operations until logout
Records of all operations performed from when a user logs in to when they log out are retained as traceability information. The past five years’ worth of traceability information is accumulated. This makes it possible to identify specific users or operations based on past historical data and determine the detailed cause should an issue occur.